Authentication in Blue
OAuth 2.0 Authentication Flow Selection in Blue
The OAuth 2.0 framework offers a versatile approach by allowing different flows to coexist within a single application, offering adaptability to diverse use cases and specific requirements. In the Blue application, strategic choices have been made to employ distinct OAuth 2.0 flows based on the nature of the tasks and the involvement of users.
Client Credential Flow for Backend Operations:
In specific backend processes, the client credential flow takes precedence. This flow caters to machine-to-machine communication scenarios, where user interaction is unnecessary. The application seamlessly communicates with authorization servers to obtain access tokens, allowing it to access resources securely and perform background tasks efficiently.
The client credential flow entails a client (such as a server-side application) authenticating itself to the API server using a client ID and secret. This authentication step is crucial to establish trust between the client and the API. Authentication methods, ranging from basic username-password systems to advanced API keys or OAuth tokens, verify the client's identity. The OAuth 2.0 client credential flow allows server-side applications to independently acquire an access token. Successful authentication establishes trust, permitting API access to requested resources or actions.
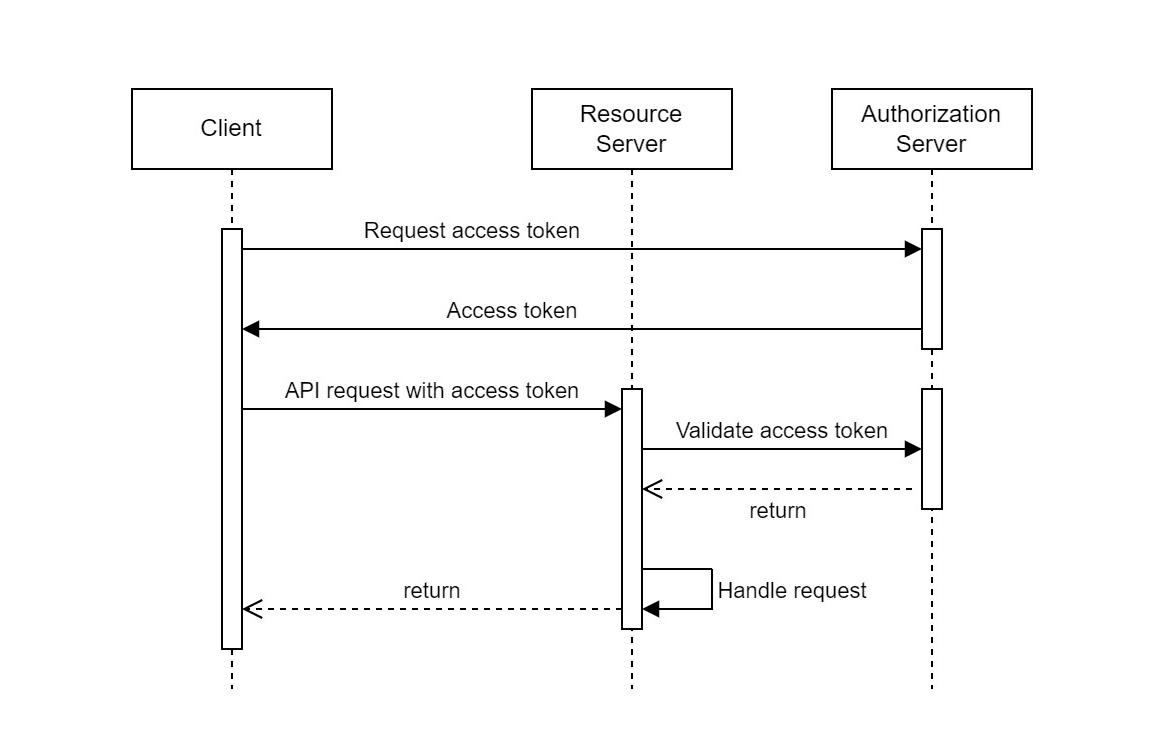
Resource server initiates a handshake with authorization server, supplying vital parameters such as Client ID, Client Secret, grant_type, and scope. Client can get these vital parameters from the Explorance team. In this context, client_id signifies the client ID for the registering application, client_secret represents the application’s client secret, scope defines the granted scopes for the access token, and grant_type specifies the utilized flow, consistently set as client_credentials. Authorization server validates the provided Client ID and Secret, subsequently issuing an access token.
The access token, a short-lived credential issued by the identity provider following successful authentication and authorization, serves to authorize client applications to access protected resources on behalf of authenticated users, eliminating the need for user credentials in each request. With the access token, users can invoke public APIs by including them in the headers.
Benefits of client credentials flow:
Utilizing the OAuth 2.0 client credentials flow offers a dual advantage compared to relying solely on basic authentication with API keys. Firstly, it enables the standardization of your API infrastructure, allowing for uniformity regardless of whether the request originates from an authenticated user or a server with a system user—thus promoting the reuse of authentication in the API. Secondly, by employing client credentials, you restrict the entities to which you disclose the credentials. In OAuth, the client initiates the token retrieval process by calling the token endpoint and subsequently utilizes the obtained token to access the API. Contrastingly, relying solely on basic authentication like API keys would necessitate the client to share credentials with every API it interacts with, leading to broader exposure of the secret. In addition to these advantages, other benefits of the client credentials flow:
- Enhanced Security: Client credentials flow minimizes the exposure of sensitive information by limiting the distribution of credentials. This enhances security by reducing the number of parties privy to the authentication details.
- Scalability: The client credentials flow facilitates scalable architecture, allowing applications to efficiently request access tokens for their own resources. This scalability is particularly valuable in scenarios where multiple applications need secure access to shared resources.
- Simplified Authorization: With client credentials, the authorization process becomes streamlined, as it is solely concerned with validating the client's identity. This simplicity can lead to more efficient and straightforward authorization workflows for applications accessing their own resources.
Authorization Code Flow for User-Facing Interactions:
Contrastingly, when user interaction is a pivotal component, the authorization code flow becomes the preferred mechanism within Blue. This flow is instrumental in scenarios where user authentication and authorization are paramount, especially when the accessed resources are intricately tied to a specific user's identity. It ensures a secure and user-centric approach, providing a seamless experience for individuals interacting with the application.
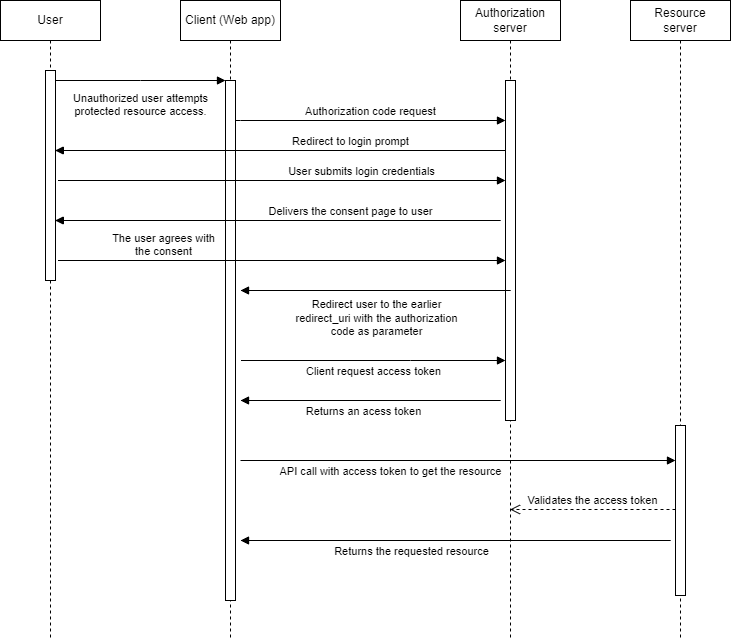
The process begins when a client application requests authorization from the user to access their resources on a resource server. The client directs the user to an authorization server, where the user is prompted to authenticate and grant or deny access to their resources. Once the user grants permission, the authorization server generates an authorization code. The authorization code is a short-lived token that acts as a one-time-use key and is sent back to the client via a secure callback or redirection URI. The client must then exchange this authorization code for an access token by making a secure, server-to-server request to the authorization server's token endpoint. Along with the authorization code, the client typically provides its authentication credentials (client ID and secret) to prove its identity. Clients can get these authentication credentials from the Explorance DIS team.
Upon successful validation of the authorization code and client credentials, the authorization server responds with an access token and, optionally, a refresh token. The access token is a bearer token that the client includes in subsequent requests to the resource server when accessing protected resources on behalf of the user. The refresh token, if provided, can be used to obtain a new access token when the original one expires without requiring the user to re authenticate. This flow enhances security by keeping sensitive information, such as user credentials and access tokens, confidentiality during the communication between the client, authorization server, and resource server. It also allows for a clear separation of concerns, with the authorization server responsible for user authentication and consent, while the resource server manages and grants access to protected resources.
Benefits of Authorization code flow
In this section, we delve into the distinct benefits that Authorization Code Flow brings to the table, shaping it into a preferred choice for secure authentication. As organizations increasingly prioritize both user experience and data security, understanding the advantages of Authorization Code Flow becomes pivotal in architecting resilient and user-centric authentication systems.
- Enhanced Security: Authorization Code Flow is considered more secure as it involves a two-step process, reducing the risk of exposing sensitive information during the authentication process.
- Reduced Exposure of Credentials: User credentials, such as passwords, are not exposed to the client, minimizing the chances of unauthorized access or credential theft.
- Efficient Single Sign-On (SSO): Authorization Code Flow supports seamless single sign-on experiences, enabling users to authenticate once and access multiple services without repeated login prompts.
- Improved User Consent Management: Users have more control and visibility into the data they are authorizing access to, enhancing trust and compliance with privacy regulations.
- Cross-Platform Compatibility: This flow is suitable for various client types, including web applications, mobile apps, and desktop applications, promoting cross-platform compatibility in authentication implementations.
By strategically employing these OAuth 2.0 flows, Blue optimizes its application architecture, aligning authentication and authorization mechanisms with the specific demands of different tasks. This nuanced approach enhances both security and user experience, showcasing the flexibility and robustness of OAuth 2.0 in diverse operational contexts.